The AAO’s complimentary lecture for February 2015 is an online reputation presentation given at the 2014 AAO Annual Session by frequent blog contributor Dr. Greg Jorgensen. Click here to begin watching.
The AAO’s complimentary lecture for February 2015 is an online reputation presentation given at the 2014 AAO Annual Session by frequent blog contributor Dr. Greg Jorgensen. Click here to begin watching.
Improve your Communication through Screen Sharing
By Dr. Doug Depew
Acworth, GA
![]() We all know how frustrating it can be to present your proposed treatment to one parent, while the other one is not present, hoping the first one will be able to make a decision by themselves. Typically however, that is not the case. More often we end up depending on Mom to carry home the dizzying array of information to discuss with Dad. And since she cannot regurgitate all you spent your time explaining, all Dad hears from her is the treatment fee, without hearing an explanation for the fee and all the wonderful things about you and your practice. In order to increase our success, screen sharing allows us to have one parent sitting in the room with you and the other virtually participating in the discussion.
We all know how frustrating it can be to present your proposed treatment to one parent, while the other one is not present, hoping the first one will be able to make a decision by themselves. Typically however, that is not the case. More often we end up depending on Mom to carry home the dizzying array of information to discuss with Dad. And since she cannot regurgitate all you spent your time explaining, all Dad hears from her is the treatment fee, without hearing an explanation for the fee and all the wonderful things about you and your practice. In order to increase our success, screen sharing allows us to have one parent sitting in the room with you and the other virtually participating in the discussion.
Screen sharing software allows users to share their computer desktop with another individual through their Internet connections. When screen sharing, the other party will see what is displayed on your entire screen in real time. It’s the next best thing to meeting with someone one-on-one. Many of us have been on the receiving end of screen sharing with some of our support companies, study clubs, or for educational experiences. How about being the person to initiate it and use it to our advantage in discussing treatment?
Some screen sharing programs are totally web-based, while others may require you to download a small program. Some programs even allow you to sketch or make annotations the remote person can see. Some vendors offer screen-sharing technology either for free or they may have a cost associated with it (per-use, monthly, or annual fee for access). Any cost is usually pretty small and worth it due to some of the extra features such as the ability to record your sessions, and the high quality images and video content you can share. In either situation, you may share patient photos, digital models, patient education videos, and images of similar cases. Although the “no cost” programs may be adequate for many doctors’ needs, there may be some limitations such as:
- You can only share with one other person at a time
- Unable to record the sessions
- Slow and jumpy video on the remote end
- No ability to annotate or mark-up the screen
So how do you go about making this happen for new patients? Well, ideally we would love to have both parents attend the initial consultation appointment. Even though we might suggest such on the initial phone call, for whatever reason, it hardly ever happens. The non-attending parent is left with the main deciding factor being the fee.
Through careful scripting during the new patient phone call, confirmation phone call, and upon arriving for their initial appointment, it may be possible to have both parents actively involved in the initial consultation. With some preparation, the second parent can be at work, in front of a computer, and be ready for a call at the appointed time. Screen sharing works best if you are on the phone with the person while sharing your screen. Once the oral exam is finished, simply have Mom call Dad from her cell phone, put him on speaker, and then have him log in to your chosen screen sharing web site by giving him the necessary access code.
In doing so, you are often able to help the parents make a decision at the time of the exam, when they otherwise would not have been able to. In the case a parent is not available at the time of the exam, you can either record that portion of the appointment and make it available to them, or make an appointment to screen share at a separate time. Screen sharing potentially can save both time and money. A second appointment is not needed, there is no need to travel, and it is much more effective explaining things using visuals than to do it verbally.
Screen sharing is also quite helpful in collaborating with our colleagues such as a patient’s general dentist or other specialists. Whether it is reviewing your treatment rationale for a patient’s dentist or navigating around different views of a cone beam CT in real-time, this technology makes it much easier to explain concepts and make joint decisions.
Screen sharing can help enhance communication by sharing information that simply cannot be done just over the phone. And if a picture is worth a thousand words, a video is certainly worth a million words. Screen sharing is a cost effective and convenient way to share our findings with a parent or colleague.
As with all things technological, the number of providers is constantly changing. A simple Google search will show several you can evaluate, many with free trials. Some of the more popular that seem to have staying power are:
- Join.me
- Beamyourscreen.com
- GotoMeeting.com
- Mikogo.com
CryptoWall Virus Affecting Practices
By Steve McEvoy, Technology Consultant
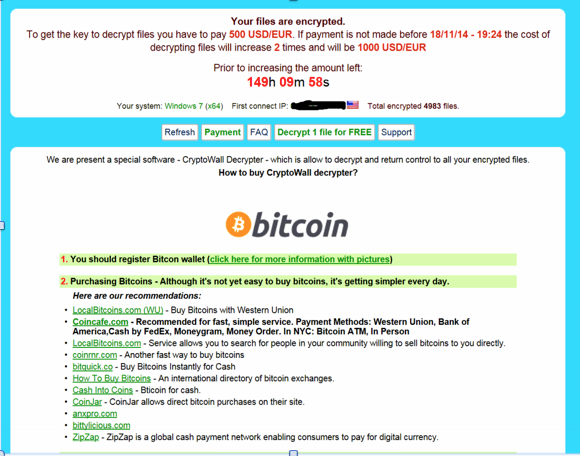
 We are seeing a fast spreading outbreak of a new virus called CryptoWall affecting many practices. Similar to the Cryptolocker virus that emerged last year, this virus seeks to encrypt all your precious data on your computer, and hold it for ransom (asking you to send them $500 USD in Bitcoin to get the decryption key).
We are seeing a fast spreading outbreak of a new virus called CryptoWall affecting many practices. Similar to the Cryptolocker virus that emerged last year, this virus seeks to encrypt all your precious data on your computer, and hold it for ransom (asking you to send them $500 USD in Bitcoin to get the decryption key).
What makes this virus so alarming is that as of a few days ago ZERO out of nearly 50 antivirus programs were able to detect it. None.
How to protect yourself
Eventually the Antivirus programs will catch up and learn how to detect it, but at this point in time you need to rely on your own wits and acting responsibly.
So far the virus has been arriving as an attachment to an email message (usually a ZIP or PDF file). We’ve seen it claiming to be airline ticket confirmations, monthly statements from the power company, shipping receipts, etc. Avoid ANY email with attachments that you are not 100% expecting. If you receive an email that you are unsure of – DON’T OPEN IT – and contact the sender by other means and confirm that they did send it to you. Reading the email doesn’t infect your PC, only opening the attachment will.
Signs that you are infected
 The virus needs time to tackle the encryption. The longer it goes undetected, the more of your data it can encrypt. You will notice the PC running much slower than normal (since it is using the computers processing power to encrypt your files). You may see files named DECRYPT_INSTRUCTION.TXT and DECRYPT_INSTRUCTION.HTML on the desktop, documents, pictures, mapped drives or any location where you have data saved.
The virus needs time to tackle the encryption. The longer it goes undetected, the more of your data it can encrypt. You will notice the PC running much slower than normal (since it is using the computers processing power to encrypt your files). You may see files named DECRYPT_INSTRUCTION.TXT and DECRYPT_INSTRUCTION.HTML on the desktop, documents, pictures, mapped drives or any location where you have data saved.
What to do if you suspect an infection
Open the DECRYPT_INSTRUCTION.HTML file and note the time remaining to decrypt your data (they only allow you a short period of time to send them the money before they destroy the data permanently). Once you have that information TURN OFF THE PC. The longer it remains online the more data it can encrypt. Do not attempt to run scans and clean the system, this only buys it more time to encrypt data. Do not connect any external drives to restore backups of data as it will attempt to encrypt your backups when it sees the drives. Contact your IT person IMMEDIATELY for their assistance in recovery.
Thin Clients in the Orthodontic Office
By Aaron Molen, DDS, MS
www.MolenOrthodontics.com
 I believe that the thin client workstation is the most underappreciated and underutilized tool in many people’s IT toolbox. A thin client is a mini-computer about the size of a paperback book that depends on an external server to perform its computations. Most of us are used to working on fat clients, which is simply another name for a personal computer that does all of its computations. Simply put, if a fat client was to lose its network connection it could still function on its own, but if a thin client loses its network connection it is dead. Why would you want a mini-computer that can’t function without a network connection? One word: scalability. Due to their size they can be placed just about anywhere; plus, because they take their orders from a central server they can be swapped out with ease and don’t require reprogramming. Adding workstations becomes easy instead of a chore and allows you to scale your practice upwards as it grows.
I believe that the thin client workstation is the most underappreciated and underutilized tool in many people’s IT toolbox. A thin client is a mini-computer about the size of a paperback book that depends on an external server to perform its computations. Most of us are used to working on fat clients, which is simply another name for a personal computer that does all of its computations. Simply put, if a fat client was to lose its network connection it could still function on its own, but if a thin client loses its network connection it is dead. Why would you want a mini-computer that can’t function without a network connection? One word: scalability. Due to their size they can be placed just about anywhere; plus, because they take their orders from a central server they can be swapped out with ease and don’t require reprogramming. Adding workstations becomes easy instead of a chore and allows you to scale your practice upwards as it grows.
I personally use Wyse thin clients, (now owned by Dell), and link them to my primary server using Microsoft’s Terminal Services. The latest thin clients even contain graphics cards which allow you to support multiple monitors and 3D imaging software. To get the best performance newer thin clients, like the Z90, should be loaded with Windows 7 RTE and then coupled with a server running Remote Desktop Services 2012 R2. When using higher end thin clients though the cost can increase per client making thin clients a great option for larger multi-location practices looking for scalability but may not offer as many benefits to a single-location practice versus traditional fat clients. There is no question though that the capabilities of thin clients have slowly blossomed under the radar and should be considered by any orthodontist looking to add workstations.
Tossing the Fax Machine and Embracing Modern Faxing
 In the modern world, hearing the dial up noise of a fax machine represents a technological step back in time. However, the widespread use of faxing will likely continue for the following reasons:
In the modern world, hearing the dial up noise of a fax machine represents a technological step back in time. However, the widespread use of faxing will likely continue for the following reasons:
- Universal Acceptance: Faxing is almost universally accepted by insurance companies and dental offices, while some do not accept emails. These fax numbers are also typically easier to locate in business directories.
- Security: Due to the point-to-point nature of fax protocol, attempts to intercept data will typically cause the transmission to fail. Therefore, faxing is generally considered secure and meets HIPAA requirements for electronic transfer of data.
- Legally Binding: The receiving machine must properly acknowledge that a fax was successful. This means that the message can legally be considered received, which is different than most other forms of electronic communication, such as email.
These benefits mean that the capability to fax is still important in the modern orthodontic office, but it does not necessarily mean a fax machine is needed. Fax machines function well, but requires a modest initial cost ($45 to $200+) and the ongoing expense of an additional phone line (~$20/month). Although it is possible to avoid an additional line by attaching a switch to an existing voice line or using a dual ring, these methods are not as consistent as a dedicated line. This option is straightforward, but are there better modern options?
Yes! Moving from traditional faxing to IP faxing (also known as internet faxing or FoIP – Fax over Internet Protocol) offers numerous benefits and less cost! It allows an orthodontic office to remove the extra phone line, get rid of a fax machine, and still utilize all the previously mentioned benefits of faxing. The switch to IP faxing has occurred slowly because previous IP faxing protocols did not interact well with traditional fax lines. However, modern protocols (T.37 for store-and-forwarding or internet faxing, and T.38 for real-time faxing) have greatly improved reliability. Options for moving to IP faxing include purchasing software for a computer or a VoIP server, buying a FoIP/VoIP server, buying an IP fax machine, or using a 3rd party online provider. All these options have certain advantages, but purchasing any equipment or software for the office will incur higher up-front costs and may need ongoing service.
Personally, I feel that most orthodontic offices should consider internet faxing using an online provider. This keeps startup costs low and requires no additional equipment (assuming you already have a computer and internet access). There are a large number of companies to choose between, so I would suggest looking into HIPAA-complaint companies with positive reviews that offer a good price for the volume of faxes sent by your office. Some providers even allow a small amount of online faxing for free (e.g. eFax, faxzero), but some of these accounts may be disabled after 30 days of inactivity. Our office currently maintains a plan for $3.49/month and $0.05 per minute of faxing (Faxage), and our monthly bill has never exceeded $6.00 – much less than the cost of a phone line. For a slightly higher base fee ($6.59/month), some companies offer integration with Dropbox, Outlook, and Google Drive (e.g. Ring Central). Overall, these online services typically offer the following advantages:
- An online portal where all incoming and outgoing faxes are stored.
- Faxing using traditional email with an attachment. (NOTE: this is sent securely from the online service, but will have the limitations of email while being emailed to the service). A receipt is emailed back when the fax is successfully sent.
- The ability to directly save the file to the computer and upload into practice management software without printing, keeping the practice paperless!
- Higher quality images than traditional faxes with the ability to print on any desired printer at your office.
- The ability to use multiple workstations to send and receive faxes.
There are two potential downsides to consider when switching to IP faxing. First, it is very easy to create a fax number, but it may take more work to maintain a current number. Second, these services typically provide T.37 store-and-forwarding faxing – meaning they hold the fax in a queue and it may take 1-2 hours to send. If these concerns are not issues for your practice, consider looking into IP faxing to inexpensively and conveniently handle your faxing needs.
Encrypting your Laptop
By Steve McEvoy, Technology Consultant
 Depending on your interpretation of the HIPAA regulations your Practice’s HIPAA policy (you have one right?) might mandate that Protected Health Information (PHI) on portable electronic devices within your Practice should be encrypted.
Depending on your interpretation of the HIPAA regulations your Practice’s HIPAA policy (you have one right?) might mandate that Protected Health Information (PHI) on portable electronic devices within your Practice should be encrypted.
Let me interpret that last sentence into English – If there is any chance that you have any information related to your patients on your laptop, it’s probably a good idea to encrypt the laptop to keep the attorneys and HIPAA Nazi’s away in the event that it is stolen or lost. You probably have your own personal data on the laptop too, so this is good for several reasons.
I would expect that if I could canvas all of you reading this article that 90+% have PHI on your laptop in some form (as minor as an email message) and less than 1% of you will have your laptop data encrypted. I expect that most laptops that get stolen or lost now don’t get reported and the Doctors are just silently hoping it doesn’t get discovered.
You want to encrypt your laptop, but how do you accomplish this? I’d like to be able to tell you the how to is simple “Just do this…” but I can’t. Depending on your equipment you have to consider your options. If you invest the time to read through the article below the conclusions at the bottom will get you started on getting this done.
The Background that Matters
Encryption is basically a process where data stored on a computer is scrambled in a pattern using an encryption key. The process is complicated, but renders the information useless to anyone unless they possess the key.
There are various levels of encryption, you might have heard of it described as 128 or 256 bit encryption. This is referring to the length of the key. A key is a string of 0’s and 1’s (binary language) and the bits mentioned describe how many characters there are. For example, 8 bit encryption would be 2 to the power of 8 possible combinations of 0’s and 1’s, so 256 possible keys if you do the math. If you used 8 bit encryption it would be pretty easy to just try each of the 256 keys to unlock your data. Now consider that 128 bit encryption has 3.438 possible keys, specifically 340,282,366,920,938,463,463,374,607,431,768,211,456. That is a lot! 256 bit encryption has 1.1577 possible keys, and is generally considered unhackable (unless you’re the NSA). Fun fact – many banking websites now use 2048 bit encryption!
I’ve heard rumors that the number of bits used matters to HIPAA, but I have NOT been able to confirm for myself. The rumor goes that 128 bit is NOT good enough for safe harbor. ‘Safe harbor’ meaning that if you lose it you don’t have to report it. It suggests that 256 bit is good enough for safe harbor. Personally I think any level of encryption will keep your data safe since no one is likely to invest the time or effort to decrypt Dental records. They are going to take your stolen laptop, reload Windows and resell it on eBay or Craigslist for a quick buck.
If we agree that we want encryption and we’ll go with 256 bit, now what? It gets tricky here, so hang in with me.
Your two choices for Encryption
The encryption process (taking your data and mashing it up using the encryption algorithm with your key) takes computing power. Something has to actually ‘do’ all that work. That something can be one of two methods generally:
- Software based encryption that has a little program plugged into Windows that is converting all the information on the fly, and thus this method uses some of your laptops CPU power and memory to get it done.
- This is great because it is a solution that can work on any computer, in particular those that don’t have the special hardware.
- On older laptops this can make them feel even slower (noticeably so) and can turn it from marginal to use to no fun at all to use. Some older laptops just can’t deal with the load. I’ve seen it make a cheap 5 year old laptop nearly unusable.
- There is some cost to this usually, ranging from free to perhaps $130.
- Hardware based encryption is a solution where there is a special encryption chip (either on the hard drive storing the data or within the laptop) to do all the thinking. This method doesn’t borrow any resources from your laptop’s CPU or memory.
- This is great since it won’t slow down your computer, even if it’s an older model.
- Even new computers or hard drives don’t all have this hardware standard – you need to look for it. When you order a new Dell or HP business laptop you need to select a hard drive with Opal security. The cost increase is minimal, typical $20 to $50.
Software encryption is appealing to many since Microsoft began to include BitLocker for free in specific versions starting with Windows Vista. There are only two versions of Windows Vista/7 that do include it, Ultimate and Enterprise editions. Unfortunately the vast majority of Windows 7 out there is Home or Professional editions. You can do an ‘In Place Upgrade’ of Windows 7 Professional to Ultimate, but it costs ~$130. The good news comes in Windows 8 – Microsoft now includes BitLocker as standard in both the Pro and Enterprise versions of Windows 8. So, if you have Windows 7 Ultimate, Enterprise or Windows 8 Pro version on your laptop enabling software encryption is as easy as going to Control Panel and clicking on BitLocker and following the prompts. Allow from a few hours to 2 days for the initial encryption to complete (knowing you need to leave the laptop alone and plugged in for that period). Pay close attention to the performance impact after BitLocker is setup. If you can’t notice the difference you are in great shape. If performance sucks afterwards, you can always turn it off and go back to normal again.
It is possible to replace your old slow hard drive with a new drive that includes hardware encryption. A fancy super-fast Solid State Drive (SSD) with Opal security can be had for as little as $114 now (I am a big fan of the Samsung 840 Pro, and others like Intel make good units). The move to SSD will likely speed up your laptop substantially in general so it might be worth it on its own. Remember to factor in the cost of having your IT person help you copy your old drive to the new one and enable the encryption.
Just because you have an Opal compliant drive installed doesn’t mean it’s turned on. Something has to work with it to turn it on and provide a key. Unfortunately Windows 7 Ultimate and Enterprise editions can ONLY do software encryption – they have no idea about Opal drives or what to do with it. The good news is that Windows 8 BitLocker now has the intelligence to work with Opal drives and can control it for you. So, Windows 7 BitLocker you will get Software encryptions only, Windows 8 you can get Software or Hardware if your drive is compliant.
There are more Software encryption options than Windows BitLocker. As with many Microsoft features, BitLocker is sort of the bare bones of what is needed. Third party companies such as Dell and Sophos have add-in applications for Windows that can do the same thing as BitLocker, maybe even better with less of a performance impact. Dell Data Protection Encryption (DDPE) is available in several versions, but for about $50 you can add it to any version of Windows and turn on Software OR hardware encryption if you drive is compliant.
Auditing
None of these personal solutions may be truly 100% HIPAA compliant. If you believe that there needs to be a constant level of electronic auditing to be able to prove that your laptop was encrypted at the moment of loss, you need a better solution. DDPE for example has an ‘Enterprise’ level license that will include this kind of auditing, but at a cost. The individual license cost only goes up marginally, to perhaps $80, but you need to have an armada of Server software running somewhere that does the auditing process and an IT person to set it all up.
Personally I think this is overkill, and if your Practice’s HIPAA policy states that you shall BitLocker 256 bit encrypt, and you do it, just write a letter to yourself (or from your IT person) that states that “On this date we enabled 256 bit Bitlocker encryption on Laptop with serial number 1234, and stored the encryption key in this safe place” and sign it. Keep this document someplace safe. You could add a periodic audit to this on an annual basis where you check that BitLocker is enabled (remember that it can be as easily turned off as it was to turn on) and document that you checked on the specific date.
Caveats
Really, really, really read this section and follow its suggestions. It’s based on the school of hard knocks I have personally attended.
Backup
If you enable encryption on your laptop I guarantee you this will cause a nightmare for your IT person down the road if you have a hardware failure (like a drive failure, Windows corruption due to spyware or virus, etc). I have lived this multiple times. Without encryption, IT people have a substantial bag of tricks to try and recover fragments of data from your dead or dying hard drive (most of the time we can get part or all of your data back). With encryption, the drive thinks your IT person is just a bad guy and works to prevent access. So, all those precious family photos or lectures you’ve prepared are at risk of complete loss.
You need a regular backup of your laptop data. We all know you should be doing this already, but rarely does anyone take the time to do it. If you are, kudos to you!
My suggestion is to invest in an Internet Backup solution for your laptop in order to keep a near real-time backup copy of your data on your drive. Other than the initial setup (which is very easy), you don’t need to do anything else. It will just run in the background anytime you are connected to the Internet. The solutions are cheap now from companies like Carbonite, Mozy and Oak Tree Storage. A personal plan from Carbonite with unlimited storage is just $5 per month now, less than a quad shot vente latte at your favorite coffee shop. [One of you is going to ask “Is an Internet Backup HIPAA Compliant?” and that is a good questions but I don’t have space to answer here in detail other than “Probably Yes”]
Make sure your backup is complete BEFORE you turn on the encryption. An Internet backup might take from a few hours to a few weeks to complete the initial sync depending on how much data you have.
Don’t Lose your Key!
Regardless of what method of encryption you enable, all of the solutions are going to need to store a copy of the encryption key. Some solutions might use a special chip on your laptop called a Trusted Platform Module (TPM chip), and others might want you to attach a USB thumb drive. If you use a thumb drive, just get a drive specifically for this purpose (they cost as little as $10 now) and then store the USB drive in a safe place (like a safe or lock box). Label the drive what it’s for “Encryption Key for my Laptop” and DON’T carry this drive around or use it like a regular USB key for your files, etc. Think about it, if you lose the key someone has a critical part of your encryption process. You might be able to make a copy of the encryption key file in several safe places (like a folder on your laptop that is then sucked up in the Internet backup).
Don’t keep the only copy on your laptop thinking that the encrypted drive is the safest place. When the drive fails, your IT person will be asking you for a copy and you will be stuck with your keys locked in the car essentially. Another reason you might need a copy on USB key is that some laptops can sense ‘tampering’ and will lock themselves down if they think someone is trying something fishy to hack the encryption. The only way to unlock the drive and get your laptop functioning again will be to present the encryption key.
Encrypt it All or Don’t Bother
Some solutions offer you a way to have just an encrypted folder or similar setup where only a portion of the laptop hard drive is encrypted. It wouldn’t take much of a lawyer to tear you apart on this, essentially requiring you to prove that there was no possibility of there being PHI on the unprotected portion of the drive. Don’t use a half measure – use a solution that encrypts the entire drive.
A Password is Essential
There isn’t much point to encrypting your laptop if you don’t have a good password on your Laptop. Imagine if your laptop was set to just automatically login without stopping for a username and password. The thief would have direct access to your data without even needing to consider hacking the encryption. Make sure you have a strong password. Check out our previous Blog post on this.
What about Mac’s?
I am no Mac expert so I won’t try to be. A little research with Google points out that the latest versions of the Mac OS now include FIleVault2 (it appears that all you need to do is just enable it). It will fully encrypt you Mac hard drive at the 128 bit level. I don’t know if this is Software or Hardware encryption. I am not sure how this will play with Mac’s setup with BootCamp partitions, but I suggest you do a little research or enlist your Mac genius of needed. I’d still advise that you make sure you have a full regular backup in place.
What Would I Do?
Ok, you’ve suffered through the entire article to get to this. Here’s what I would do based on a few scenarios:
- If I had an older laptop I was ready to replace – get a new laptop with Opal drive included and Windows 8 Pro and then enable BitLocker
- If I had a decent existing laptop on a Windows version that already included BitLocker, I would just enable Software encryption and know the performance hit will be a little bit but not enough to matter
- If I had a decent existing laptop on a version of Windows that did NOT include BitLocker and I didn’t want to replace the drive and OS (due to the hassles) I would get a third party encryption application like Dell Date Protection Engine (DDPE) or Sophos and setup software encryption.
- If I had a decent existing laptop and was willing to upgrade the hardware and OS, I would get a new fancy SSD with Opal drive and then install Windows 8 Pro and use BitLocker to control it.
- For any of these solutions I would add the Do-It-Yourself auditing to document the setup was completed and periodically review that it’s still enabled.
- I would be sure to keep one copy of the encryption key on a USB drive in my safe, and another copy in a folder on my encrypted drive that would also get backed up by my Internet Backup plan.
If I had done one of these scenarios and my laptop was lost or stolen, I would rest easy that the data was safe.
Electronic Records Transfer: Do You Use E-mail to Transfer Records? Is it HIPAA Compliant?
What is “Big Data” and How Is It Related to the Practice of Orthodontics?
 By Anthony M. Puntillo DDS, MSD
By Anthony M. Puntillo DDS, MSD
Have you heard of the term “Big Data”? My guess is that for many orthodontists the term is likely a bit like the term “The Cloud.” They may have a general idea of the concept, but are not entirely sure how it is or will be important to them. In fact, there is a strong relationship between the two terms that I will discuss later in this article. First, however let’s look at “Big Data” by itself. According to Wikipedia “Big data is a blanket term for any collection of data sets so large and complex that it becomes difficult to process using on-hand data management tools or traditional data processing applications.”
In 2009 the United States Congress passed the American Recovery and Reinvestment Act (ARRA) which included the Health Information and Technology for Economic and Clinical Health Act (HITECH). [For a detailed summary of this legislation please see Kirt Simmons blog posting from July 9, 2012 “The Electronic Patient Record: How it Affects the Private Practitioner”]. One of the requirements of HITECH is that full implementation of electronic health records (EHRs) for all patients is required by 2016. The requirements of this act specifically pertain to healthcare providers who participate in the Medicare and Medicaid programs. That means that currently few dentists are covered by this mandate. However, this does not mean that we are not being affected. Since 2009 doctors and hospitals across the country have spent billions of dollars, with the help of government subsidies, converting paper based systems to electronic digitally based health records. These new digital systems are now collecting vast amounts of valuable data related to patient care. Much of this information was collected before the legislation, but in a paper non-standardized format that was not easily aggregated and retrievable for meaningful analysis. The value of all of this collected digital data is only beginning to be fully understood. Big Data from all healthcare providers is being aggregated and programs to analyze the data are being used to improve the quality, safety, and efficiency patient care. Hospitals are examining treatment protocols and doctors are making better informed treatment decisions based on the previous care of thousands of similar patients.
As I stated earlier, the EHR requirement of HITECH does not specifically pertain to most orthodontists so why is this important to us? Many orthodontists have or are now also in the process of converting their practices to paperless systems (without the assistance of the government money). Several of the orthodontic specific software vendors offer cloud based systems and here is where “Big Data” and “The Cloud” come together. The aggregation of data from hundreds or thousands of individual private orthodontic practices into cloud servers is beginning to open the door for data analysis (mining). Just think about how valuable that information can be to our patients and practices. Most of the research studies published in our journals today involve treatment samples of less than one hundred. The biannual Journal of Clinical Orthodontics Practice Study generally relies on the input for a few hundred survey responders (out of a possible pool of more than 8,000). Wouldn’t it be helpful for us to know the most efficient type of Class II corrector based on the actual metrics collected from the previous care of thousands of patients treated in practices all across the country or the globe? Wouldn’t the knowledge that your treatment times/appointments vary significantly from the national or regional averages be useful? There is little question that access to “Big Data” analytics will offer our profession the opportunity to improve treatment quality, safety and efficiency for our patients just as it is beginning to do for the other fields of healthcare.
Tips & Tricks for the Digital Office
There are several quick and easy technologies available to help you update your office without breaking the bank. Two of my personal favorites are thin clients and dual screens. I believe that the thin client workstation is the most underappreciated and underutilized tool in many people’s IT toolbox. A thin client is a mini-computer about the size of a paperback book that depends on an external server to perform its computations. Most of us are used to working on fat clients, which is simply another name for a personal computer that does all of its own computations. Simply put, if a fat client was to lose its network connection it could still function on its own, but if a thin client loses its network connection, it is dead. Why would you want a mini-computer that can’t function without a network connection? Two words: cost & scalability.  Thin clients cost half as much as a traditional computer and due to their size can be placed just about anywhere. Because they take their orders from a central server, they can be swapped out with ease and don’t require reprogramming. Adding workstations becomes easy instead of a chore and allows you to scale your practice upwards as it grows. I personally use Wyse (now owned by Dell) thin clients and link them to my primary server using Microsoft’s Terminal Services. The latest thin clients even contain graphics cards which allow you to support multiple monitors and 3D imaging software. The capabilities of thin clients have slowly blossomed under the radar and should be considered by any orthodontist looking to add workstations.
Thin clients cost half as much as a traditional computer and due to their size can be placed just about anywhere. Because they take their orders from a central server, they can be swapped out with ease and don’t require reprogramming. Adding workstations becomes easy instead of a chore and allows you to scale your practice upwards as it grows. I personally use Wyse (now owned by Dell) thin clients and link them to my primary server using Microsoft’s Terminal Services. The latest thin clients even contain graphics cards which allow you to support multiple monitors and 3D imaging software. The capabilities of thin clients have slowly blossomed under the radar and should be considered by any orthodontist looking to add workstations.
The idea of dual screens may seem simple but it’s vastly underutilized within orthodontic offices. Though there is a period of adjustment the efficiency and productivity of your team members will increase once they begin using dual monitors at their workstations. Though many offices have placed dual monitors in their doctor’s personal office they sometime underestimate the benefits of equipping their administrative and clinical teams with the same technology. Having the ability to keep imaging software up on one screen and management software up on another is indispensable in my mind. Most computers and thin clients support dual screens and those that don’t can be easily retrofitted to support them using an inexpensive PCI card. There’s also no reason to settle for just two monitors. If two is good, then at some workstations, three or four screens may be even better.
You’re Missing Something Important… (…in your backup)
Steve McEvoy, Technology Consultant

The first thing I check when I start to work with a new Practice is their backup. Most Practices have something in place, but more often than not I find the single most important piece of data is being missed – the Practice Management Database. Imagine if your Server crashed and you had to use your backup to recover all your precious data, and at the end of the recovery your IT person explains “There you go, it’s all restored – oh – except for your Practice management data that is lost forever!” Your Practice would be severely impacted and the financial loss would be enormous. Taking 4 minutes to read the rest of this article and then pass it along to your IT person.
The Challenge
Most backup routines merely come along and make duplicate copies of files sitting on your hard drive. Imagine creating a Microsoft Word document. First create a new blank Word document and save it to your desktop. Open it, type a few new paragraphs, but you leave it open and don’t save it to the hard drive. If you run the backup right now, the backup will catch the new empty document that is saved and completely misses the newer data still in memory (but not saved to disk yet).
Many Practice Management programs (such as Dolphin, Orthotrac and Ortho2 for example – listed alphabetically) use a sophisticated database called Microsoft SQL Server. Backing up SQL Server needs a special technique. Just like in the Word document example, SQL Server is always open and keeps the latest changes to your information in memory or log files. If you just come along and ‘copy’ the database files you won’t have anything useful to recover with (bad news!). This is usually what I find is happening, people are running backups but aren’t realizing they need to take extra steps to backup the SQL database.
The Solution
The Practice Management companies know about the challenge and all of them have documented solutions for you to follow. The problem is who actually reads the manuals? This is a case where you (or your IT person) needs to. Ask your IT person directly “Are you properly backing up the Microsoft SQL Server database that my program uses?” If they don’t know for sure the answer is ‘yes’, the simple solution is to ask them to call the support team of your Practice Management Software company and ask for a little advice. They will have a solution:
- Dolphin has a ‘Safe Backup’ solution that can run automatically as part of your end of day or end of month
- Orthotrac has a database backup routine that can be set to run automatically and keeps copies of the database for each day of the week.
- Ortho2 has a database backup application that can be setup to run as often as you like.
You’ll notice in my descriptions there are a lot of ‘cans’. You have to be sure these are setup and working. Make sure the backup files that these routines make are then swept up in your routine file copy backups. In a crisis, these backup files can be recovered from your regular backup and then the SQL database can be restored.
Final Thoughts
If you use a Cloud based Practice Management you don’t have to worry, they are doing it for you. If you use an Internet Backup the same problem can exist. Many Internet backup companies like Carbonite.com and Mozy.com don’t normally backup SQL databases, so you should check this out since your SQL database is your most important piece of data worth backing up. Personally I would recommend you take an extra step – make your own SQL database backup in addition to the one you configure with the Practice Management Software. Microsoft SQL Server includes the ability to schedule SQL backup jobs on its own, and I would recommend that you setup two backups (one at noon, one in the evening). Two backups are better than one!